Network Security
Pivot Point Security provides network security services to help organizations protect their data, systems, and networks from cyber threats. Our team of experienced professionals will work together with your organization to conduct the necessary assessments (e.g, vulnerability assessments, penetration testing, clou security posture assessments) necessary to meet your security and attestation requirements. With Pivot Point Security’s CREST accreditation and network security expertise you will achieve a provably secure and compliant network/cloud security posture.
What is Network Security?
Organizations often need to prove their network is secure and must accomplish this with limited resources. By assessing your network security, we can provide you with a comprehensive remediation strategy and an understanding of your overall risk. Clients who work with us can prove to key stakeholders their network is secure and know how to prioritize valuable resources.
Testing network security and infrastructure comes in a few flavors depending on your current security posture and where you would like to be. Based on those factors we can recommend the best course of action for you to reach your desired level of security & prove it to key stakeholders.
Network Security Assessment Methods:
- Vulnerability Assessment
- Penetration Testing
- Architecture Review
Where Does Network Security Begin?
No matter your title, you are reading this because you are in charge of ensuring your network is secure. If you are like any of our clients, how well you accomplish this is extremely important to both your personal success and your organization’s success.
Finding the time and resources to accurately decipher how secure your network is can be a major problem. Because of that, the biggest challenge we see our clients face is knowing how to prioritize their valuable resources. We often hear the question, “Where should I begin?”
The Starting Line…
By partnering with Pivot Point, you will know exactly where to begin. We use a risk centric tiering strategy to categorize your network vulnerabilities based on their criticality to your business. You will have a clear understanding of where to begin and a roadmap to arrive at your preferred destination.
Our team of consultants has over 20 years of Network Security experience and our client’s success is directly related to our proven process.
Our Proven Network Security Consulting Process:
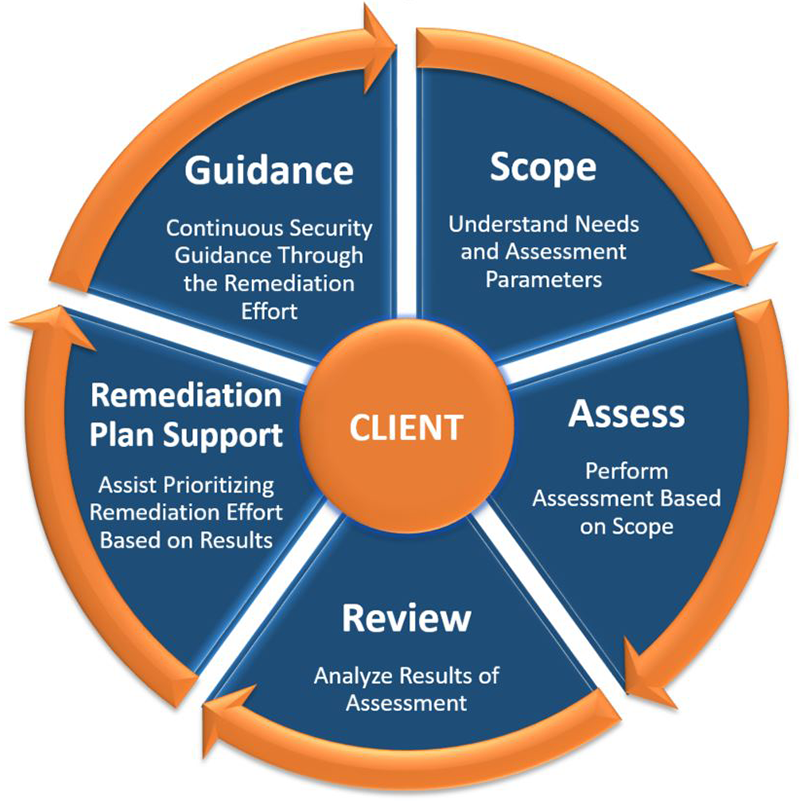
Why Choose Us?
Our Approach
We base our approach on what our clients care about…
- Want to rotate pen testers every year? No problem, we do it for you… we never have the same tester approach your system two years in a row. There is no need to search for a new pen tester every year which will save you time.
- Want security metrics? No problem, we track them for you… since we are testing your system on a consistent basis we have benchmarks for where we began, what was fixed and what still needs to be addressed. Expect actionable security metrics for IT Managers to gauge progress, manage priorities and continuously improve.
Our Staff
Every consultant you speak to is a full-time employee. We believe staffing our organization with quality full-time experts gives our clients a level of service a one-and-done contractor cannot provide.
Our Process
Your business is unique and brings its own unique challenges; however, our Proven Process is successful across all industries, organization sizes & corporate cultures.
Click here to talk with a SERVICE expert.
The Result?
Peace-of-mind. You can rest easy knowing your organization is secure and you can prove it.
Otherwise…
Operating your organization without knowing your network is secure leaves your organization one disaster away from closing the doors. There is too much at stake to leave your business so vulnerable.
With that in mind:
We don’t pretend we are the only group of quality Network Security consultants but we do feel it’s crucial for you to be protected. If we are not the right partner for you, we would be happy to help point you in the direction that most clearly aligns with your goals and objectives.
The security of your operations and continuation of your organization is what we care about. If you would like to learn more about working with our team, contact us here:
Network Security FAQs:
A vulnerability assessment (VA) is an automated way to gather data about issues on your network, such as missing patches or bad configurations. A penetration test almost always includes a VA to inform the testing. It uses the VA and other data obtained via reconnaissance to attempt to exploit any vulnerabilities identified and gain some level of unintended access to systems or data.
So, while a VA will inform you on “how vulnerable you are,” a penetration test will inform you as to whether those vulnerabilities can be exploited and, if so, what the impact could be to your organization.
You really can’t, just as you can’t really tell if a colonoscopy was a good one. The best way to ensure you have a “good” penetration test is to verify that the vendor has an independent attestation regarding the quality of their methodology and the individuals doing the testing (e.g., CREST certification).
The scope of a penetration test should be determined using a risk based approach. What assets do you need to protect? From whom? Where do those assets reside (e.g., cloud, DMZ, external/public systems, internal network segments)? What laws/regulations apply (e.g., PCI-DSS). These basic questions will help frame the pen test scope.
CREST Network Penetration Testing
Penetration testing is a critical part of many security programs across industries and is mandated by a growing number of security and privacy regulations, including HIPAA and PCI-DSS. Choosing the right service provider to meet your specific penetration testing needs is critical for compliance, and also to identify and mitigate risks to your data, applications, infrastructure and users.
Network Vulnerability Assessment
An organization’s network is one of its most important tools—one that must deliver consistent performance, reliability and security for the business to remain operational.
To make sure their networks remain secure, organizations can run network vulnerability assessments (VAs) to identify configuration errors, missing patches, and unregistered assets in an automated and economical manner.
Network Penetration Testing
Network penetration testing, a type of ethical hacking, is a method of evaluating the security of your network using simulated attacks to identify and exploit vulnerabilities in your network infrastructure. Malicious attacks are simulated using a variety of manual techniques supported by automated tools. Our penetration testing methodology goes beyond the detection process of simple scanning software to identify and prioritize the most vulnerable areas of your network and recommend actionable solutions.
Network Architecture Review
A Network Architecture Review is a review and analysis of relevant network artifacts (e.g. network diagrams, security requirements, technology inventory, DMZ ) to identify how the network architecture and controls protect critical assets, sensitive data stores and business-critical interconnections in accordance with the organization’s business and security objectives.

