An information security gap assessment or gap analysis is a key task for nearly every organization, because it tells you where your information security program is right now versus where you want it to be going forward. For example, you might need to compare your current control environment to the compliance requirements for ISO 27001 or some other best-practice framework.
Done correctly, a gap assessment illuminates risks and vulnerabilities you might not be aware of, and can help reorient your InfoSec program if your investments are not aligned with business goals. A gap assessment is also a critical element in a comprehensive information security risk assessment.
But many organizations struggle to perform successful gap assessments. The process is often unduly time-consuming, and requires considerable expertise and objectivity. The “gap” is also by definition a moving target because both your control environment and desired “end state” frequently change due to impacts from new threats, technology, business opportunities, etc.
Having performed thousands of gap assessments with clients across industries for 20+ years, we’ve often seen significant efforts yield inadequate or even misleading results that create blind spots of risk and set businesses up to fail compliance audits or suffer a data breach.
What is a gap assessment?
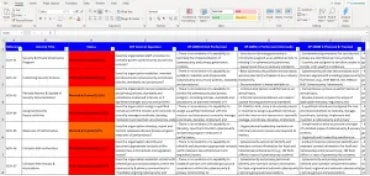
A gap assessment can be as straightforward as starting with a list of requirements/controls (e.g., the DoD’s Cybersecurity Maturity Model Certification framework) and ticking off which of the controls you’ve implemented and which you haven’t. The latter group constitutes your “gap.”
What a gap assessment doesn’t tell you is whether you actually need to implement a particular control based on your actual risks, vulnerabilities, risk appetite and business environment. Most information security frameworks (NIST 800-171 being a notable exception) aren’t “one size fits all,” but are meant to be applied based on what your unique scenario actually calls for.
What is a gap assessment template?
While gap assessment can be a complex, time-consuming, challenging and ongoing process, a gap assessment template can help save time and improve results.
A gap assessment template is a tool that organizes and simplifies the process of comparing your current information security controls to a best-practice control framework.
Here are four ways that a gap assessment template can streamline your gap assessment process:
- A gap assessment template can give you an “out-of-the-box” framework that you can apply across your unique technical, business and product/service environments without “reinventing the wheel.”
- A gap assessment template can reduce the time and effort your organization needs to identify missing controls.
- A gap assessment template can support ongoing gap assessments by making it easier to flag changes in your “as-is” and/or “as-desired” state(s) based on specific changes in your “risk universe;” e.g., moving sensitive data to the cloud, complying with a new privacy regulation, more employees working from home, etc.
- We’ve all heard the truism, “When all you have is a hammer, everything starts to look like a nail.” A gap assessment template helps reduce inherent experiential bias to eliminate analytical “blind spots.”
By effectively leveraging a gap assessment template, your organization can end up with a more objective and higher quality gap assessment result with less time and effort—ultimately enabling you to further reduce information security risk.
Our Accelerated Risk Management (ARM) Expert System
Leveraging our longstanding experience conducting risk assessments, Pivot Point Security has developed an expert system that drives a paradigm shift in risk assessment—a better end result in less time and with fewer resources.
Starting with client inputs plus our proprietary threat and vulnerability libraries, our Accelerated Risk Management (ARM) tool automatically calculates how every pertinent threat agent could act on each vulnerability in your environment, and for each of your data types (e.g., employee health data, customer data, intellectual property, etc.). For each data type, ARM calculates the likelihood that a threat can act on a vulnerability and what the impact might be.
One of the results of that process is a gap assessment, which compares your current/inherent risks versus remaining/residual risks after mitigation based on your ratings for the maturity (on a 1-to-5 scale) of your current controls. From there, you’ll know how much your risk has been reduced, and where your risk is still too high and should be reduced further.
In addition to leveraging our ARM tool, you can download our free gap assessment template based on the ISO 27001 controls. These “umbrella” controls cover the requirements for many of the information security standards that you may be subject to, such as PCI-DSS or HIPAA.
What is a risk assessment?
You don’t want to burn time and resources implementing and operating controls you don’t need. In fact, this can actually increase your risk. Further, you don’t want to continue to operate existing controls that aren’t bringing you demonstrable risk reduction benefits.
How can you find out what controls you need to implement or fix, why you need those controls and how strong they need to be? That takes a risk assessment, which generally requires more time, effort and expertise than a gap assessment. But the two go hand-in-hand.
When you perform a risk assessment, you determine/estimate the threats your organization faces, the impact to your organization of a given threat manifesting, and the likelihood of that happening based on your vulnerabilities.
This allows you to rank or quantify your risks and prioritize risk treatments (e.g., implement 2FA, buy cyber liability insurance, keep certain data on-premises versus the cloud, etc.). That prioritized action plan, in turn, yields a risk-driven basis and business justification for what controls to actually implement from your gap assessment.
What’s next?
Want to find out more about our better, faster and cheaper gap assessment methodology?
Interested in a better, faster and cheaper risk assessment process? To download your free risk assessment template, click here.
And check out this quick video on how to use our risk assessment template and paradigm-busting ARM tool.
For more information:
- What’s the difference between a risk assessment and a gap assessment?
- How we’ve adapted our ARM tool for vendor risk management
- Balancing objectivity and subjectivity in risk assessment
- How to rank your InfoSec risks
- Advice to optimize your ongoing risk assessment process