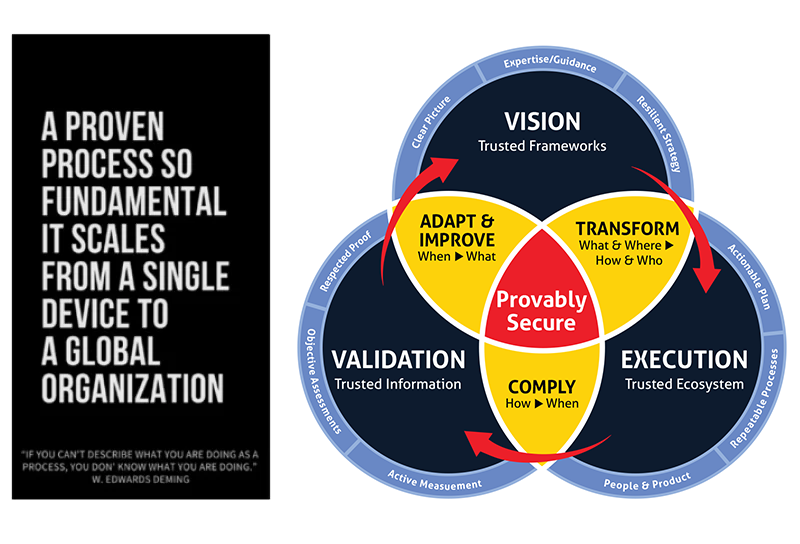
Partnering with Pivot Point Security
Continuous and consistent execution of your Information Security controls requires the RIGHT people (qualifications, knowledge, domain expertise, vertical experience) and the RIGHT products (quantities, costs, efficiencies, effectiveness). Building a Trusted Ecosystem (both internal and external to your organization) simplifies the journey to “secure and compliant.” Pivot Point Security’s Trusted Ecosystem provides significant business benefits:
Leveraging the trusted relationships we have forged and vetted over our 20+ year history reduces the level of effort and the risk of a sub-optimal vendor selection which in turn:
Naturally aligns your vendors with the trusted frameworks that are proven for your use case and industry
Reduces time to certification/target cybersecurity position, business and information security risk
Provides greater cost certainty
Our Trusted Ecosystem includes product vendors, service providers, and key regulators/influencers – for example:
Audit firms (e.g., Registrars, CPA firms, PE firms, law firms)
Information Security Vendors (e.g., Vulnerability Scanners, code scanners, SIEM/SOC, etc.)
Information Security Services Vendors (e.g., MSSP, Security Assessors, Pen Testers)
Industry regulators (e.g., ABA, SEC, CMMCAB)
Trusted Framework providers (e.g., OWASP, ISO, NIST)
Industry Influencers (e.g., Trade Associations, publications)
IT Product and Service Vendors with high infosec requirements (e.g., Document Management Systems, secure email, network infrastructure, cloud service providers, manages service providers)
—
Please reach out if you think your organization can add value to our Trusted Ecosystem and we can add value to yours. Pivot Point Security is committed to developing “win-win-win” (end client, ecosystem member, PPS) relationships.
CMMC Certification Guide
A Simple Guide to Comply with the DoD’s Cybersecurity Maturity Model Certification (CMMC)
This CMMC Certification Guide will give you a quick and easily digestible introduction to the CMMC and the process we use to help our clients become CMMC compliant.