CMMC Assessment Checklist
How can you get the ball rolling internally towards achieving CMMC readiness at your organization? That’s a question we hope to help you answer with our CMMC Assessment Checklist. This high-level outline with links to additional resources will empower your group to take strategic and informed action on CMMC readiness.
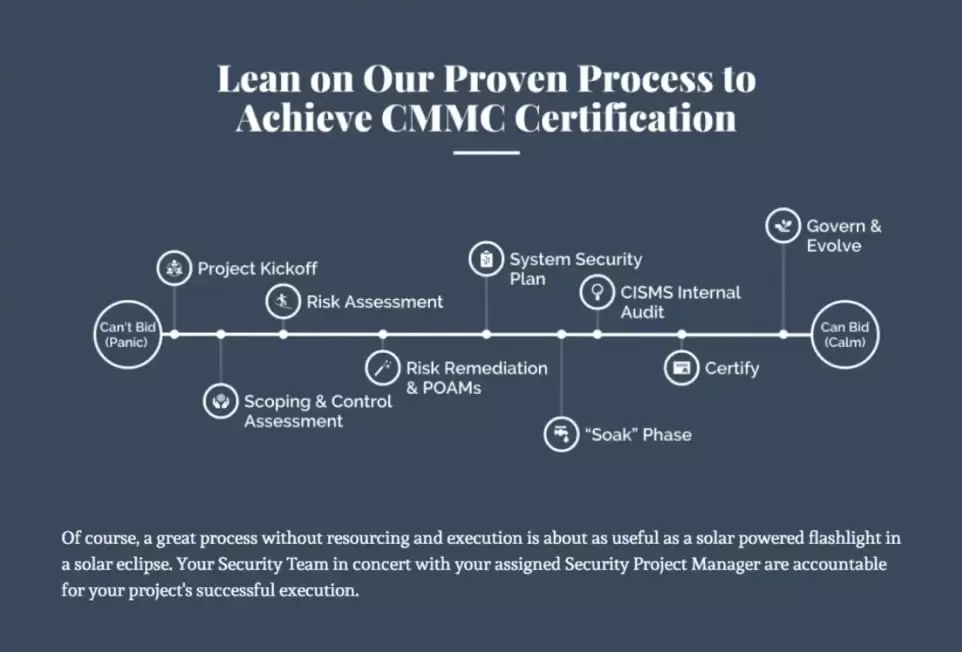
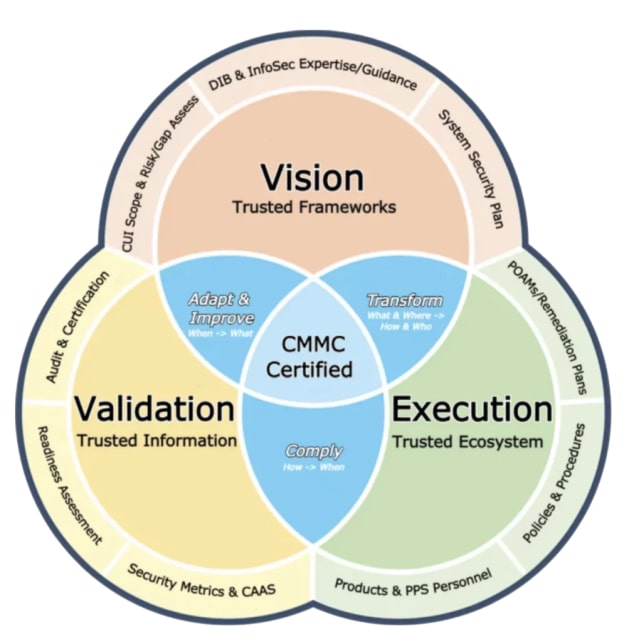
We also thought it would be valuable to mention our Pivot Point Security “Proven Process” — an action-based framework that will guide you in a positive direction and simplify your CMMC journey. Use our Proven Process in concert with the resources identified in this CMMC Assessment Checklist to guide your NIST SP 800-171 and CMMC efforts.
1. Perform a CMMC Scoping, Risk Assessment, and Control Maturity Assessment
You’ll need to understand where federal contract information (FCI) and controlled unclassified information (CUI) controls are required and which systems need to be protected. Ideally, you will work with an internal or external resource with government contracting and NIST expertise to ensure that you develop a clear picture of where you are and where you need to go. Identify relevant artifacts (e.g., existing policies, network diagrams) and conduct scoping interviews with a broad cross-section of the organization to understand how FCI and CUI flow to, within, and from your organization. Any systems/applications/locations/personnel/subcontractors that store, process, or transit CUI are in your CUI scope (e.g., CUI relevant). You’ll also need to understand other information security requirements (e.g., DFARS obligations, ITAR), known risks, and the maturity of your CMMC relevant controls. This step is essential to establishing the scope of your CMMC System Security Plan (SSP).
2. Develop an initial System Security Plan (SSP)
The SSP is critical to documenting the security controls that are in place for all the systems that are CUI relevant, and it is a requirement for CMMC compliance. The initial SSP should focus on the data flow diagrams, system boundaries, asset lists, stakeholders lists, system interconnections, etc.
3. Drive Risk Remediation & Document your Policies
The bulk of preparing for CMMC will be working to remediate risks and close the gaps identified during the Scoping, Risk Assessment, and Control Maturity Assessment phase. Remediation will include developing extensive documentation and implementing supporting technologies (e.g., multi-factor authentication, SIEM, secure email/file sharing, mobile device management) needed to stand up your CUI enclave. You should document policies and maintain a standard operating procedures document that “enables individuals to perform them (CMMC practices/requirements) in a repeatable manner.”
4. “Finalize” Your System Security Plan (SSP)
Now that your CUI enclave is up and operationalized, you should be in a position to finalize the SSP.
5. Conduct a CMMC Readiness Assessment (CRA)
Ensuring you have what you need for a successful CMMC certification assessment is best done by validating your readiness. Have an appropriately qualified and independent person (or team) conduct your CRA using the same standards for evidence. As necessary, you may need to implement Plans of Actions and Milestones (POAMs) to drive closure on open issues identified during your CRA to ensure your certification assessment is a success.
Pivot Point Security: Leading Information Security Assessment and Consulting Firm Since 2001
Since 2001, Pivot Point Security has been helping public sector and commercial organizations understand and effectively manage their information security risk. We work as a logical extension of your team, simplifying the complexities of security and compliance. We are a CMMC Registered Provider Organization (RPO) that has helped thousands of organizations build cybersecurity programs that comply with government and industry regulations. We will make sure that we understand your DFARS obligations and address all things DIB, including DFARS 7012, NIST SP 800-171, SPRS, and CMMC Level 3.
A Proven Process Tuned To Address The Unique Needs Of The Defense Supply Chain
Since 2001, Pivot Point Security has been helping public sector and commercial organizations understand and effectively manage their information security risk. We work as a logical extension of your team, simplifying the complexities of security and compliance. We are a CMMC Registered Provider Organization (RPO) that has helped thousands of organizations build cybersecurity programs that comply with government and industry regulations. We will make sure that we understand your DFARS obligations and address all things DIB, including DFARS 7012, NIST SP 800-171, SPRS, and CMMC Level 3.