Build a CIS CSC Aligned Information Security Program
The CIS CSC is built to give a simple answer to a complex problem.
Problem – With so many security challenges AND so many ways to defend against them, what should an organization do?
Answer – Focus on a prioritized list of 20 simple controls to combat against the most common threats.
Organizations who adopt these controls gain a simple framework to improve information security and cyber defenses.
A little more complexity – followed by a little more simplicity
Depending on your industry there are dozens of frameworks to choose from (ISO 27002, NIST, HITRUST, CSA Stars, etc.) to manage security effectively. At first blush, another is more noise, not less.
So, how do you choose the right one for you?
I’ll be honest, I like the approach the CIS is taking. They are saying, as an information security community, we know how to defend ourselves from threats; however, we are getting in our own way. CIS is putting forth a simple, somewhat tactical approach to getting to a pretty strong security posture.
Helping Orgs Strategize InfoSec Initiatives is What We Do
For over 20 years we have led hundreds of firms to reach their security goals with the first step often being; which security framework(s) would be most beneficial to our business? But enough about us… let’s ask a more important question.
Why the CIS CSC may be a good option for you?
In short, these controls can provide value to most organizations
✔ For a smaller organization with limited security it’s a simple, scalable, approach to building a basic program and improving it over time. The three levels of implementation guidance provide a logical construct that provides both a near and longer-term action plan.
✔For a larger or smaller organization with a reasonably strong security posture it can be used to augment current security practices. Frameworks like ISO 27001 and SOC 2 are excellent approaches to building a comprehensive security program, however, their required flexibility reduces the specificity of their guidance. We sometimes use CIS CSC during ISO 27001 Internal Audits or SOC 2 readiness assessments to provide a more prescriptive reference for the auditor.
✔ It’s worth noting that CIS CSC tends to be particularly appealing to IT professionals moving into security as it takes a very technical and tactical approach to security.
Can I guess what you are thinking?
“Okay, implementing these controls sounds pretty easy, perhaps a little too easy. Is that all I need to do? What does a bigger framework like NIST or ISO 27001 cover that CIS CSC doesn’t? Can I get CSC certified? Or should I still be looking to get an ISO 27001 certification or a SOC 2 Type II audit report?”
This is where a 30-minute conversation with one of our experts can replace hours of research. Every organization is unique and the intricacies of the data you collect/process, the regulations you are subject to, the demands you are getting from customers/vendors/management, etc. all come into play. Use this link to schedule your “THIS IS NOT A SALES CALL” call with experts on our team that can point you in the right direction.
FAQ’s
What controls does the CIS CSC include?
CIS CSC Version 7.1 (released in April 2019) consists of the following information security controls:
CSC 1: Inventory of Authorized and Unauthorized Devices
CSC 2: Inventory of Authorized and Unauthorized Software
CSC 3: Secure Configurations for Hardware and Software on Mobile Devices, Laptops, Workstations, and Servers
CSC 4: Continuous Vulnerability Assessment and Remediation
CSC 5: Controlled Use of Administrative Privileges
CSC 6: Maintenance, Monitoring, and Analysis of Audit Logs
CSC 7: Email and Web Browser Protections
CSC 8: Malware Defenses
CSC 9: Limitation and Control of Network Ports, Protocols, and Services
CSC 10: Data Recovery Capability
CSC 11: Secure Configurations for Network Devices such as Firewalls, Routers, and Switches
CSC 12: Boundary Defense
CSC 13: Data Protection
CSC 14: Controlled Access Based on the Need to Know
CSC 15: Wireless Access Control
CSC 16: Account Monitoring and Control
CSC 17: Security Skills Assessment and Appropriate Training to Fill Gaps
CSC 18: Application Software Security
CSC 19: Incident Response and Management
CSC 20: Penetration Tests and Red Team Exercises
Why would we choose CIS CSC over other information security frameworks?
The goal of the CIS CSC is to answer the question, “What do we need to do to stop the most common, known attacks.” A distinguishing feature of the CIS CSC is that the controls are prioritized and focused on ensuring maximum risk reduction for resources utilized. The CSCs are based on the most prevalent attack patterns from leading threat intelligence. The controls are updated as new attack patterns are identified and analyzed by leading security researchers. The CIS CSC appeals to very technical information technology/information security personnel as it is a very technically oriented approach to information security.
Benefits of Our As-A-Service Model:
✔ Move forward at your own pace – Dedicated CIS CSC expertise ensures you have the staff and expertise you need, when you need it.
✔Establish a roadmap and stay on target – Pivot Point Security hosts weekly status/coordination/working meetings between your project team and our experts dedicated to your project.
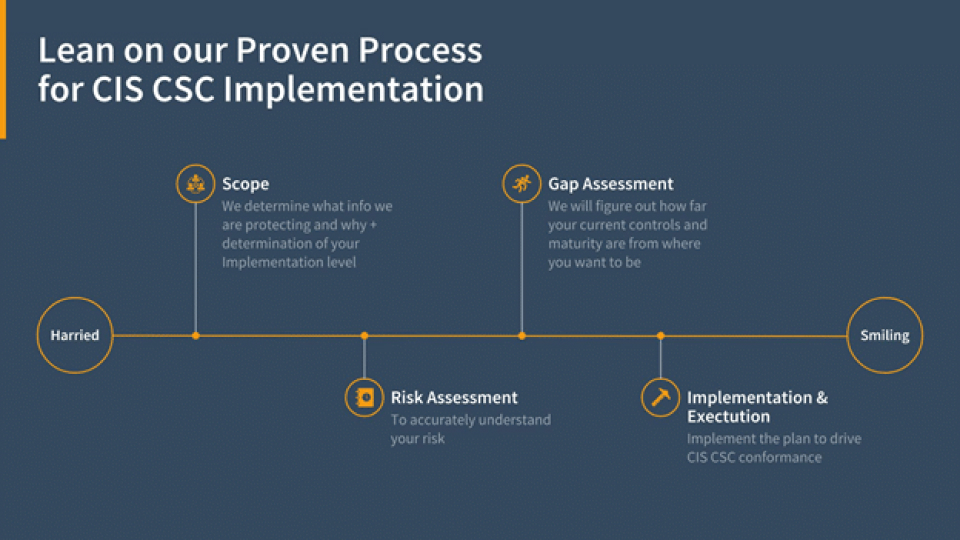
✔ Save time and money – Leveraging our expertise, proven processes and artifacts simplifies the process of implementing CIS CSC controls.
✔Ensure you meet CIS CSC guidelines – Pivot Point Security will ensure your success by validating all artifacts to guarantee they fully conform with the guidelines.
✔ Ensure CIS CSC is operationalized (not just implemented) – Pivot Point Security will help build/support your information security steering committee and chair committee meetings. Depending on your industry there are dozens of frameworks to choose from (ISO 27002, NIST, HITRUST, CSA Stars, etc.) to manage security effectively. At first blush, another is more noise, not less.