Last Updated on January 30, 2025
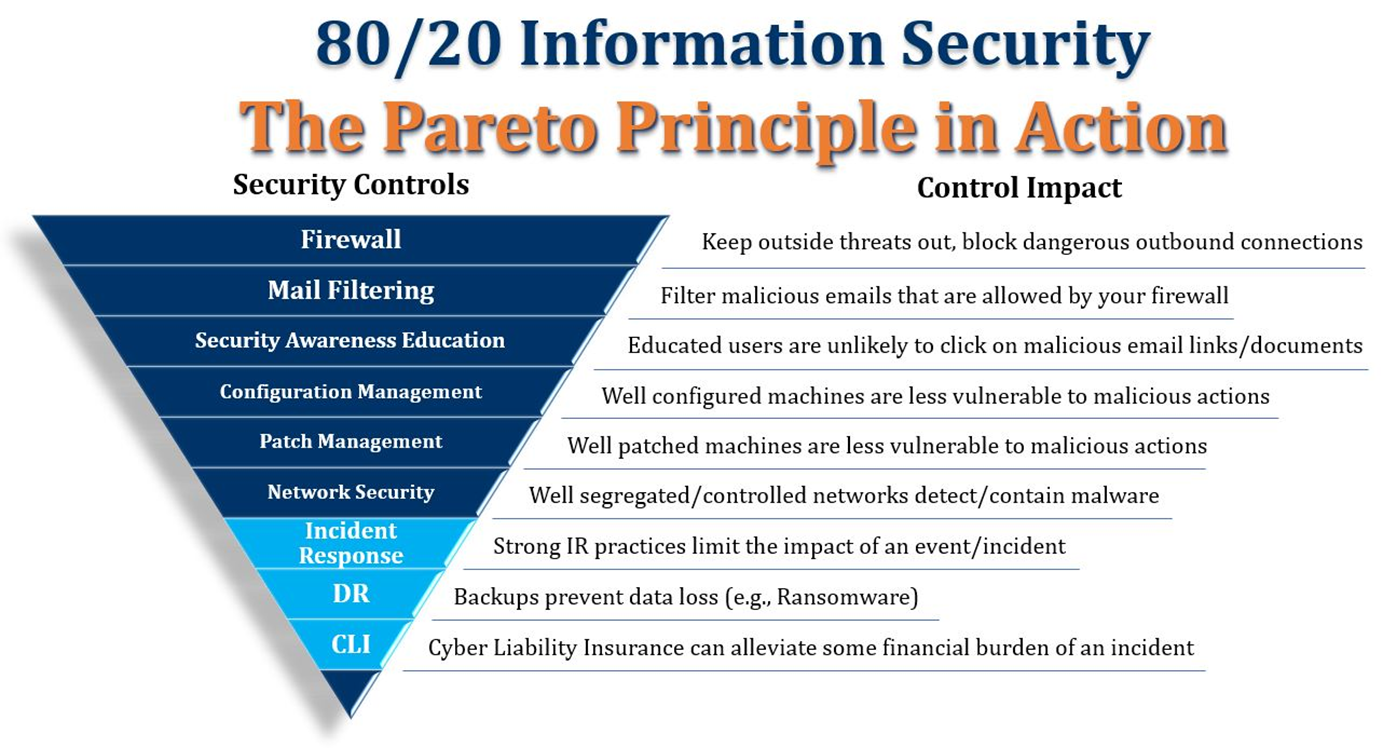
If you’ve been following along with this multi-part post, you’ve seen how to mitigate about 80% of your InfoSec risk with 20% of the effort by systematically tackling your biggest risk—social engineering/phishing attacks.
In this part 4, I’ll cover the final 3 controls in the 80/20 approach:
- Incident response
- Disaster recovery/backup
- Cyber liability insurance (CLI)
These final three controls work together to greatly reduce the potential damage from an attack that has managed to breach your layered defenses and is loose on your network.
Control #7: Incident response
Even with robust network security in place, you still need an incident response (IR) plan in case malware breaks out despite your precautions. Your goal is to reduce detection/response time to minimize the number of hosts that are impacted, and in the case of ransomware minimize the number of files that are encrypted.
Do your end users know what to do if something “bad or weird” starts happening on their desktop, like a message popping up that says “You’ve been infected!” or the mouse cursor starting to move on its own? What do they do first? Turn off the machine? Call the help desk? Light their desktop on fire? These initial responses are often critical in controlling the damage.
Likewise, do the people users are communicating with know what to do? Do they know what your cyber liability insurance policy says to do and not do? Do these “first responders” know what they’re authorized to do and the right steps to take in the right order? For example, do they know who to call to report an incident (your MSP, your company attorney, the FBI, an information security firm you have on call)?
If you don’t have an IR plan (or if you have one but haven’t communicated it), chaos may reign at the worst possible time. Conversely, the impact-reducing benefit of an IR plan that works can be massive.
Control #8: Disaster recovery/backup
Worst-case, despite your controls and your IR plan, a phishing attack has introduced ransomware that has run amok in your environment. Every single file that anybody’s worked on in the last three years is now encrypted and the attackers want $30,000 with no guarantee you’ll ever see your data “alive” again.
Guess what? If you have current, offsite backups that are unaffected by the ransomware, you can just re-image your machines and recover your data from backups. Despite the fact that everything went wrong, the impact of the breach is limited, and you can resume normal business operations pretty quickly.
Control #9: Cyber liability insurance
Cyber liability insurance (CLI) adds a layer of protection should an incident occur that exposes Personally Identifiable Information (PII), or otherwise makes you subject to data breach notification regulations. CLI can’t mitigate the full impact of a breach when it comes to your customer base and brand reputation, but it can mitigate the financial impact significantly.
Key takeaways
If you’ve been reading along through these posts, you’re probably ready for a recap. Here are the key takeaways:
- Roughly 80% or more of the cyber risk that threatens your organization comes from email by phishing type attacks.
- You can implement and optimize a very short list of controls such that with about 20% of the effort you can reduce or eliminate 80% or more of your risk.
- The key to success is to focus your efforts on reducing social engineering/phishing related risk as described in these posts. This is what will drive the 80/20 value proposition.
Access all posts in this series here: