Last Updated on January 31, 2025
One of my favorite historical figures is Vilfredo Pareto; an Italian engineer, economist, sociologist, political scientist and philosopher. He developed what is now called “The Pareto Principle,” also known as the 80/20 rule, the law of the vital few, or the principle of factor sparsity. The principle states that, for many events, roughly 80% of the effects come from 20% of the causes.
Pareto originally developed the concept in relation to the distribution of income and wealth among the human population. But it can be observed in virtually every segment of life. For example, 80% of your business comes from 20% of your customers, 80% of the orders in a restaurant are for 20% of the items on the menu, in rush hour 80% of the people are on 20% of the roads, and so on.
Is there a way to leverage the Pareto Principle in information security? Indeed there is!
We don’t have to look far to see the Pareto Principle in action in InfoSec. Most studies report that in around 80-90% of all data breaches, social engineering (usually phishing) is involved.
So logically, if we can eliminate or significantly reduce the risk from that 80% of attacks—and we do it by implementing just a handful of targeted, focused and related controls—then we’d be able to mitigate 80% of an organization’s information security risk with 20% of the effort.
…But you’ve saved a lot of time and budget and are now “almost there.”
Figure 1 illustrates this “80/20 cyber security approach,” which describes a mutually supportive series of controls to address social engineering related risk.
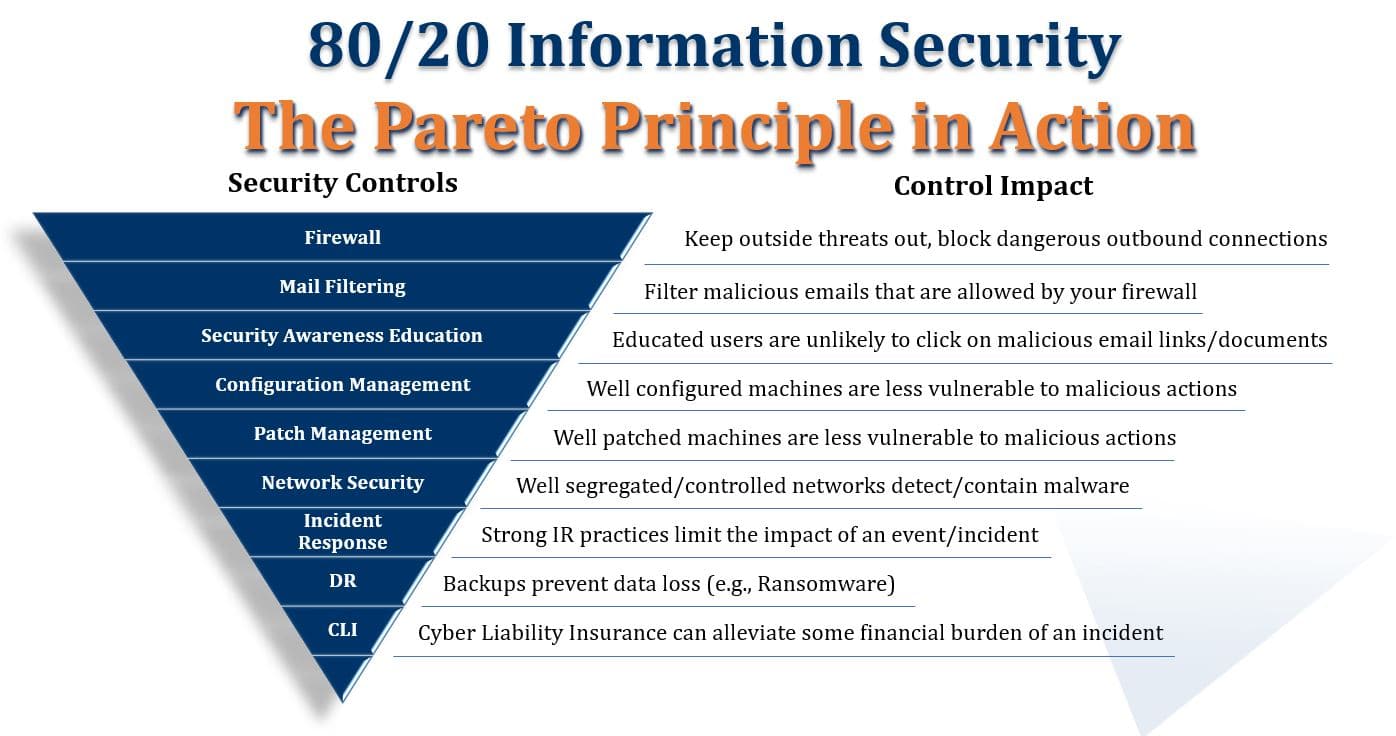
Because it doesn’t address “the other 20%” of InfoSec risk directly, this approach might not be ideal for a business with a mature information security posture that is looking to conduct an all-inclusive risk assessment and then implement controls to mitigate all those risks.
But it’s perfect for many small to medium businesses (including municipalities, schools and nonprofits) looking to optimize their available time, money and expertise to make the biggest impact with the least effort—hopefully 80% or more of the “bang” for 20% or less of the “buck.”
Are you “done” with information security at that point? Most likely not, as the remaining risk might well be more than your organization can accept. But you’ve saved a lot of time and budget and are now “almost there.” Which means you’ll find it much faster and easier to get to the place of being “provably secure,” if that’s your goal.
I hope this post has piqued your interest in the 80/20 cyber security approach. In upcoming posts I’ll explain each of the 80/20 controls and how they work together to mitigate the risk from social engineering/phishing attacks.
Access all posts in this series here:























