Last Updated on February 4, 2025
For the last 20 months or so, we’ve worked with nearly 200 government municipalities on cyber loss control projects, now largely completed. Data security is a major concern for many municipal governments, so in this post—the fourth in our Cyber Security Foundation for Municipal Government series—we would like to explore the key controls municipalities need to combat malware—especially ransomware—and social engineering attacks.
Local Government is Vulnerable
Let’s start with a wakeup call. Knowing them to be vulnerable, hackers are specifically targeting municipal governments and K-12 schools for ransomware attacks. Consider these statistics:
- According to the Cisco 2017 Annual Cybersecurity Report, ransomware attacks are escalating at an annual rate of 350%.
- According to IBM, the average ransomware demand is between $500 and $2,000.
- Symantec research shows that 64% of US ransomware victims pay the ransom, but only 47% actually recover their files. This means the “price ceiling” will keep going up.
- In October 2017 the US Department of Education warned K-12 schools that the Dark Overlord group and other hackers were directing extortion and ransomware attacks at schools.
- Government (6%) and education (13%) lead the pack among industry verticals in terms of the percentage of organizations infected with ransomware.
How to Avoid Attacks
What can you do to keep your municipality safe? While the spectrum and number of attacks is vast, you can dodge almost all of them by doing these four things consistently:
- Ensure all systems are patched. Windows update will handle most things but also be sure to update Chrome, Firefox, Adobe, etc.
- Ensure systems are configured optimally Keep antivirus software up-and-running and up-to-date on all your computers. Enable click-to-play plugins in all your users’ web browsers to keep Flash, Java and other plugin content from running automatically as soon as a webpage opens. This makes it easier to block malicious malvertising ads that can scare or dupe users into downloading malware. (It can also improve page load times, reduce CPU usage and conserve download bandwidth.)
- Minimize admin level access on desktops.
- Have recent backups. Ransomware is nothing more than a nuisance if you have recent backups.
- Have a basic Incident Response Plan. Ensure users and your IT teams know what to do if and when something goes wrong.
- Educate your users so they don’t fall victim to phishing emails! Many such emails have “telltale signs” that can put users on alert, such as:
- They have to do with money.
- They make you an offer that’s too good to be true.
- They bring up “urgent issues” to trick users into making hasty decisions.
- They request personal information.
- The “To” line isn’t addressed to the user specifically.
- There are misspelled words, bad grammar and other mistakes.
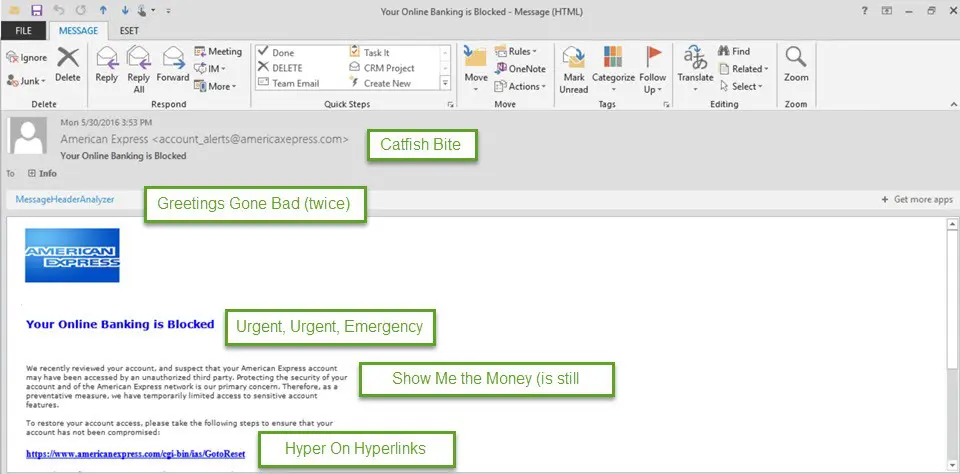
The graphic below illustrates what a typical phishing email looks like.
To get help dealing with a ransomware or malware attack right now, or for expert advice on next steps to keep your municipality safe from cyber threats, contact Pivot Point Security.
We also invite you to download our free eGuide, “Cybersecurity Foundation for Municipal Governments.”
In our next post, we’ll blog on cyber awareness education: what it is, how it works and why it’s so important for municipal organizations. Until then… stay tuned and stay safe!
Ongoing Series: Cyber Security Foundation for Municipal Governments
We are overviewing this foundational cyber security guidance for municipalities in a series of blog posts. The full list of topics we will be covering includes:
- Covering the bases
- Password management and access control
- Backup and encryption
- Malware and social engineering attacks (CURRENT POST)
- Cyber security awareness education
- Contingency planning: Incident response, disaster recovery and business continuity
- Vendor risk management
- Patching and other “technical controls”