Last Updated on April 14, 2025
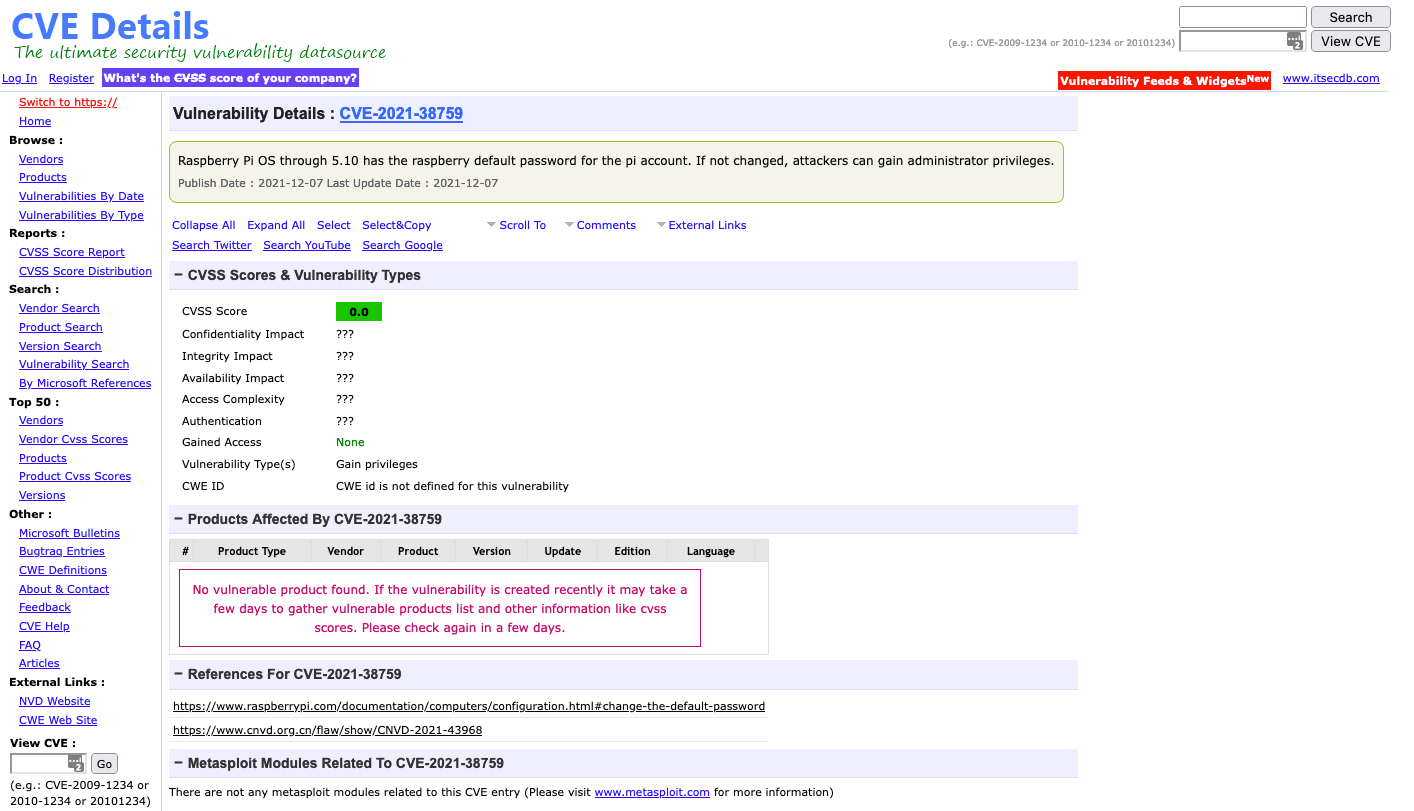
Twitter and various InfoSec outlets just blew up over a CVE (Common Vulnerabilities and Exposures) database entry CVE-2021-38759 published on December 7, 2021, noting that Raspberry Pi OS utilized a default password that, if not changed, could be leveraged by attackers to gain administrator privileges. Here’s a screenshot of the CVE:
My first thought was, “This was ridiculous!”, which has been the reaction of many of my peers as well. Next thing you know, there will be a CVE issued because fire is hot.
A Raspberry Pi is a small, single-board computer, initially designed to promote basic computer science education in schools and developing countries (see Figure 2). Raspberry Pi OS (formerly named Raspbian) is one of the many operating systems available for installation on a Raspberry Pi. To “install” the OS, you essentially copy it to an SD card, insert it, and power on the Raspberry Pi. The unit’s creators determined that the easiest way (remember schools and developing countries) to do that was to create an OS image with a default user account. This way, once powered on, you could log in to your Raspberry Pi and do cool things.
Raspberry Pis are very handy little computers. Over the years, as their adoption has grown, so has the size and complexity of the projects that utilize them. However, they were never intended to be used in a production environment. So why potentially compromise their ease of use over a bogus CVE?
We had a good laugh on Teams about this CVE and at the (at least) two people involved in its submission. Then I started thinking about the implications… We penetration testers speak with developers a lot, and a good percentage of them want something like a CVE identifier to acknowledge that a finding is a vulnerability before they’ll address it. Yes, these types of developers make us want to bang our heads against the wall. However, if something as silly as adding a CVE number to the finding makes them fix it without argument, I’m all for it. Hell, it took forever for Cisco to stop shipping devices with the default cisco/cisco login, and they make devices designed for production.
While a CVE for default passwords on an operating system and device that shouldn’t ever be in a production environment is funny… … if it gets people talking—and taking action—about getting rid of default passwords in general, the world would be a more secure place… right?
What’s Next?
Ready for a password-free future? Here’s a blog post you’ll love: https://www.pivotpointsecurity.com/blog/transitioning-to-a-post-password-future-with-owasp-asvs-v4/
Concerned about password reuse across your production apps? You’re not alone: https://www.pivotpointsecurity.com/blog/reusing-passwords-security-tips/