Last Updated on November 20, 2025
Organizations in the US defense industrial base (DIB) that plan to pursue Cybersecurity Maturity Model Certification (CMMC) 2.0 compliance are behind the curve if they are not actively “closing the gap” between their current controls and the requirements for their chosen CMMC level.
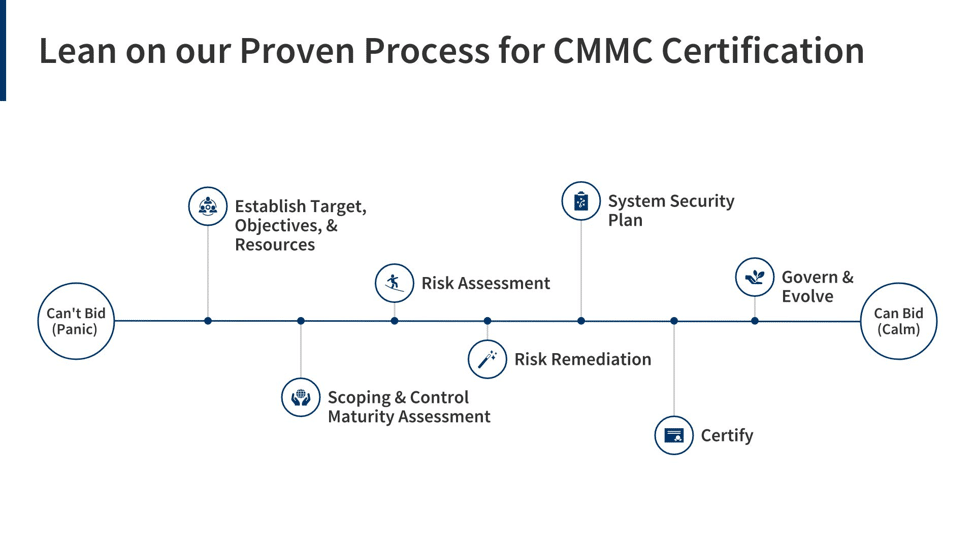
While other activities must come first, as discussed below, a gap assessment is a critical early step for any business approaching CMMC compliance at Level 2 (Advanced) or Level 3 (Expert). Can you get the accurate and comprehensive assessment results you need with internal resources, or should you consider hiring a third-party expert? This short post considers both options.
Which CMMC level should we pursue?
The first step towards CMMC for any defense supplier is to identify their CMMC level. There are several key inputs to this decision:
- If your current contract specifies NIST 800-171 compliance, then, at least in the eyes of the US government, you handle controlled unclassified information (CUI). NIST 800-171 compliance is equivalent to CMMC Level 2.
- If your current contract has a DFARS 7012 clause, then you are likewise deemed to handle CUI and most likely need a CMMC Level 2 certification.
- Are you looking to pursue future business on projects that require receiving CUI from the DoD? Achieving CMMC Level 2 certification now would be a significant advantage.
- If you participate in a “highest priority” DoD program (e.g., missile guidance) and need to protect CUI from advanced persistent threats (APTs), then you need to comply with CMMC Level 3.
- If you know you only handle Federal Contract Information (FCI) to fulfill your DoD contracts, then you may only need to comply with CMMC Level 1 (Foundational), which requires just 17 controls.
What is our CMMC scope?
Along with identifying your CMMC level, you need to define the scope of your CMMC environment as a preliminary step toward gap assessment. Scoping determines the subset of your overall IT infrastructure that will be subject to assessment for CMMC compliance.
CMMC’s purpose is to protect CUI. Therefore, CMMC scoping is all about knowing what CUI you handle, where it resides, and what assets (systems, processes, people, including third-party assets) store, transmit, process, or create CUI. Questions to ask include:
- Where does CUI enter our environment?
- Where is it stored?
- How is it processed?
- Do we create any CUI?
- How does it exit our systems and where does it go?
- How is it archived or destroyed?
Using this information, you can diagram your CUI data flows and identify the assets associated with those flows. This activity illuminates the boundaries of your CMMC compliance environment, often called a CMMC enclave.
Why can’t we start with a gap assessment?
A gap assessment identifies the gaps between your current cybersecurity posture and a set of requirements, such as CMMC Level 1, 2, or 3. So why not pick a CMMC level and perform a gap assessment based on the corresponding controls?
You want to conduct your scoping exercise before your gap assessment because how you implement CMMC—or any other comprehensive cybersecurity framework—is strongly impacted by your scope and the identified risks you face. Therefore, by definition, you cannot accurately assess gaps until you define the scope.
Nor can you fully assess gaps until you assess risks. Until you know the risk level you must mitigate, you won’t know how robust an associated control needs to be.
For example, you know you handle CUI, so you start your CMMC certification journey with a gap assessment against CMMC Level 2. Based on those results, you undertake a $50,000/multi-month migration to the Microsoft 365 GCC “government cloud” to meet CMMC Level 2 requirements. But because you didn’t initially scope your CUI environment, you recognize too late that some of your CUI is subject to International Traffic in Arms Regulations (ITAR). Because of the extra security that ITAR requires, you actually needed to implement Microsoft 365 GCC High to achieve CMMC Level 2 certification. The cost and effort for your original migration have thus been wasted, and you need to migrate yet again.
Should we do our CMMC gap assessment in-house?
If you have strong in-house cybersecurity expertise, you can save money by conducting a DIY CMMC gap assessment. Here are some factors to consider:
- If your business is already NIST 800-171 compliant and has posted a valid score to that effect in the DoD’s Supplier Performance Risk System (SPRS), you probably have the people, processes, and systems in place to confirm CMMC compliance internally. You’re also much more likely to have compliance reporting in place to support your gap assessment than if your cybersecurity was less mature.
- If you think you’re “close” to NIST 800-171 compliance (approximately 80% of controls), an in-house gap assessment can work, provided you have an accurate system security plan (SSP) and a formal risk assessment program in place as starting points. These are critical governance elements that help ensure you understand your true cybersecurity posture.
- If you’re “far” from NIST 800-171 compliance, you may not be ready for a gap assessment. Every CMMC certification project must follow a logical, structured approach to ensure the results meet business goals. To provide context for a gap assessment, you first need to define your CUI scope, determine whether it can be reduced, and then conduct a risk assessment. Many SMBs lack scoping and risk assessment experience and would benefit from third-party guidance to set them up for success.
What are the advantages of leveraging a third party for CMMC gap assessment?
Some of the benefits to engaging an external resource for your CMMC gap assessment effort include:
- You get an independent, objective evaluation of how well your cybersecurity controls are performing, based on an unbiased approach. If your in-house team implemented a control incorrectly or incompletely, will they have the expertise to identify that in your gap assessment?
- As a stepping stone to CMMC certification, a third-party gap assessor can provide an attestation of your security posture that you can use to demonstrate NIST 800-171 or CMMC alignment or conformance to a prime contractor or government agency.
- An independent gap assessment report can help provide “safe harbor” if you have a cybersecurity incident that exposes CUI or are subject to a legal complaint regarding your cybersecurity. The US Department of Justice (DoJ) has settled numerous False Claims Act actions targeting cybersecurity, including three in 2024 totaling $4.25 million. These suppliers were deemed to have “misrepresented… to the government the extent to which it had equipment required by the regulations and instituted the required security controls…”
- With a third-party gap assessment, the vendor can provide specialized expertise to evaluate operational technology (OT), Internet of Things (IoT) assets, cloud-based services, and other systems that may be in scope for your CMMC certification but are unfamiliar to your internal team.
- A third-party gap assessment demonstrates to stakeholders that your organization is serious about improving its cybersecurity posture and protecting CUI. This helps build trust and credibility because the results are supported by an impartial assessment.
What’s next?
As a CMMC Registered Provider Organization (RPO), CBIZ Pivot Point Security is here to guide your organization to a successful CMMC certification. We tailor our consulting services to your unique situation, working with you to determine what it will take for your organization to achieve and maintain compliance at your designated CMMC level.
Contact us to start a discussion with a CMMC expert.