What is a Virtual Chief Information Security Officer (vCISO)
A vCISO functions just like a full-time, onsite CISO except that they are generally remote most of the time. A vCISO helps your organization strategize, plan, and execute a robust information security program that aligns with your business strategy and goals. A vCISO combines the vision of executive leadership with the demands of securing the business by overseeing the execution of a cohesive, actionable plan.
Pivot Point Security’s vCISO service, optionally including Virtual Security Team (vST) members, is designed to fill expertise and bandwidth gaps at both advisory and tactical levels on your teams—so that achieving your cybersecurity and business objectives is a guaranteed reality. Our clients benefit from the ability to demonstrate to their customers and other key stakeholders that they are secure and in compliance with applicable regulations and/or frameworks.
Want more information on the vCISO role and how it can help your business? Check out these episodes of The Virtual CISO Podcast:
What does a vCISO do?
- Managing the information security team
- Planning for new security infrastructure in alignment with direction from the business
- Interfacing with executive management
- Attending board meetings to update your directors on the company’s security posture
- Creating policies, procedures, standards, and guidelines and running them by management for approval
- Overseeing incident response and event management activities
- Planning security awareness training around security program changes
These are just a sampling of the many tasks (we’ve counted about 50 so far!) a vCISO could be called upon to perform. With today’s collaboration tools, a vCISO can handle all of these with minimal onsite interaction.
Should we consider a vCISO?
- Need the skills of a CISO, but not full-time
- Need a strategic roadmap for security and compliance
- Dealing with a shortage of qualified security talent and struggling to retain security staff, leading to significant recruiting and HR “pain”
- Need to demonstrate to key stakeholders that your business is secure and compliant
- Lacking a clear vision of where you are now and/or where you want to go with security
- Dealing with multiple compliance requirements, particularly GDPR and/or CMMC
- You need security experience specific to your industry (e.g., SaaS, legal, financial services)
- Need security talent capable of relating with customers, your C-suite, and regulators
- Customers, management and/or partners expect that someone has the CISO role
- Need someone with a CISO, CSO or DPO title for compliance
Benefits of a vCISO
- Cost savings—Get the security expertise you need at a fraction of the cost of a full-time CISO
- Clear direction—Know where you are and where you are going on your security journey
- REDUCE THE RISK AND SEVERITY OF A DATA BREACH
- Achieve and demonstrate compliance—to differentiate you from competitors and help drive business growth
- Stronger relationships—Build trust and positive relationships with clients, suppliers, investors, senior management, and other stakeholders
- Focus—Enjoy peace of mind and focus on your business knowing that experts are focused on your security
- Dodge the security talent shortage
- Get vendor-neutral advice
- Virtual Security Team—gain on-demand access to Pivot Point Security expertise (aka “the right people”) across nearly any information security related discipline(s) as part of your vCISO engagement
Choose the right vCISO service for your needs
- Executive Information Security Advisor (EISA) only—PPS advises, you execute, you govern
- vCISO + Virtual Security Team (vST)—PPS advises, you + PPS execute, PPS governs
- vCISO + Virtual Security Team + Managed Service Provider—PPS advises; you, PPS and a suggested MSP execute; PPS governs
Executive Information Security Advisor
With our Executive Information Security Advisor (EISA) service, we provide an expert advisor, and you execute and govern your cybersecurity program. The focus is on providing the guidance you need to move your program to a “provably secure and compliant” state in 6 to 24 months.
Your advisor will guide your security lead on governing the program’s overall operation to ensure it evolves with changing contexts and achieves your business objectives. If needed, you can call on our Virtual Security Team to execute/operate controls, perform compliance functions, etc.
vCISO + Virtual Security Team
This is the option most companies go with. The focus is on providing advisory and governance services along with the operational services you need to move your cybersecurity program to a “provably secure and compliant” state in 3 to 24 months.
Your vCISO will govern your program to ensure it evolves with changing contexts and achieves your business objectives. Your in-house team along with our virtual team will jointly execute key compliance functions and operate your security controls.
vCISO + Virtual Security Team + Managed Service Provider
For firms that need added IT support, this option accelerates your progress and gives you “one throat to choke.” The focus is on providing advisory and governance services along with the operational services you need to move your cybersecurity program to a “provably secure and compliant” state in 3 to 24 months.
Your vCISO will govern your program to ensure it evolves with changing contexts and achieves your business objectives. Your in-house team along with our virtual team will jointly execute key compliance functions and operate your security controls. The MSP fills one or more IT seats on your org chart.
Our Proven Process for vCISO engagements
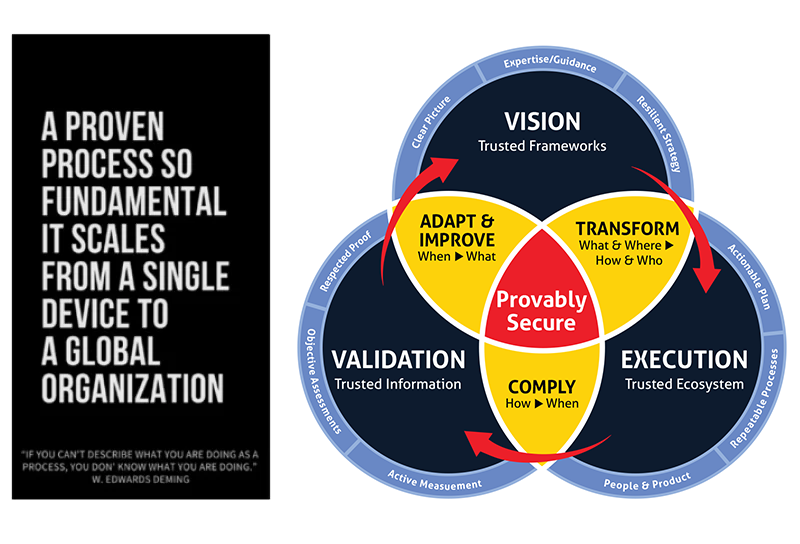
Based on our collective experience across thousands of successful information security engagements over 21+ years, Pivot Point Security has a 3-step Proven Process that we adapt and apply to everything we do.
Our core focus—serving as a trusted partner to help our clients become provably secure and compliant—sits at the center of our process. To achieve that result, four things need to happen:
1. You need a Vision of how to move from where you are to where you want to be.
2. You need the Trusted Frameworks (e.g., ISO 27001) and Trusted Ecosystem necessary to Execute your vision.
3. You need the Trusted Information necessary to Validate that you’re achieving the intended results.
4. You need a Proven Process to bring it all together.
Here’s how our Proven Process fits together.
For a quick PDF summary of our proven process, click here
For an executive briefing video on our proven process, listen to this podcast with Pivot Point Security CISO and Managing Partner, John Verry.