Last Updated on April 14, 2025
In the course of helping our clients achieve ISO 27001 certification or implement an information security management system (ISMS) or information security controls in general, one of the first things we need to do is assess their current environment. What are the threats they actually face? What aspects of the environment are vulnerable to the threats?, if a risk and a vulnerability did “intersect” as an occurrence, what would the risk impact be? And how likely is it that a specific risk would actually occur?
As we look at risks, probabilities and impacts together with clients, our overall goal is to identify the most critical areas where the business may face unacceptable risk. These areas will require the highest-priority controls you want to implement first. Simple, right?
Well… in theory the process sounds simple enough. But in practice, in order to yield meaningful results that actually protect an organization optimally and make the best use of its resources, the analysis has to be undertaken thoughtfully. Indeed, research on this process shows that reflection on risk attitudes and the subjective judgments that follow from them is one of the most critical factors often missing from risk analysis.
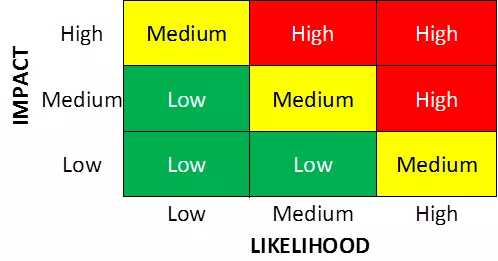
To support accurate risk assessment as well as facilitate meaningful risk discussions, Pivot Point Security recommends using a risk matrix with our clients. Especially for SMBs, and/or if this is the first time an organization has thought about risk in a structured way, notwithstanding factors to the contrary we often recommend a straightforward, 3×3 matrix like the one shown below.
This type of matrix shows event consequences along one axis (the bottom in the illustration) and event frequency or likelihood along the other (the left in this case). Each block in the matrix represents some level of risk. Blocks representing equivalent risk form “groupings” within the matrix, shown here as green, yellow and red.
A simple matrix like this can cover all kinds of risks and impacts, and to display them to support discussion, decision-making and even status tracking. Experience shows that the best results come from keeping the scales for these ratings simple and clear; e.g., low, medium and high risk probability and low, medium and high impact. (Or you can use numbers; e.g., 1, 2, 3.)
From there you can define what you want “low,” “medium” and “high” (or 1, 2 and 3) to mean. For example, a client I worked with recently defined their scale as follows:
- Low probability = Would hardly ever happen.
- Medium probability = Could happen.
- High probability = Will most likely happen.
- Low impact = One day’s worth of work with no client impact.
- Medium impact = A week’s worth of work with two out 100 clients impacted.
- High impact = An ongoing effort to remediate an issue across all clients.
Of course, anytime you’re trying to determine how probable something is that hasn’t happened yet, there is bound to be some subjectivity involved—but you try not to be arbitrary. Again, the primary goal is to identify the highest-priority risk issues that you want to remediate first.
In the case of a 3×3 matrix, “Low x Low” clearly presents the lowest risk and “High x High” the highest. The “intermediate” (yellow in the illustration) risks are more difficult to interpret/prioritize because some are directly comparable and some are not.
Every form of risk matrix has its advantages and disadvantages and there’s no “one size fits all” approach that works for every business. That’s why Pivot Point maintains an extensive library of them, along with documentation on how well they worked and why. We’ve seen just about every approach possible.
In my personal experience, in terms of matrix complexity it’s rare to see significant benefit when you go beyond 5×5. Compared with 3×3, a 5×5 matrix obviously provides more granularity/specificity as to the level of risk.
That can be useful for prioritizing risks, but definitely requires more thought and consideration to make the delineations (e.g., Critical, High, Medium, Low, Negligible) relevant due to the greater subjectivity and potentially greater communication challenges involved. On the plus side, feeling like you’ve more clearly defined the relative impact and probability of issues can enhance your ability to allocate time, money and staff to remediation efforts.
Again, risk assessment isn’t a “black-and-white” exercise. This is a big reason why it can be very useful to have skilled, experienced professionals supporting the process—especially if you prefer to use a richer framework like a 5×5 matrix.
Speaking of complexity, another factor that we often apply risk assessment to help think about impact is security areas or objectives; e.g., health & safety, financial impact, confidentiality, integrity, availability and/or reputation. Instead of just thinking about “impact” in general, we discuss impact relative to these specific areas or factors to build a more holistic risk profile. You can do this whether you’re working with a 3×3 matrix, a 5×5 matrix or no matrix at all. (You can check out a sample 5×5 matrix describing consequences across multiple objectives here.)
For example, take a hurricane (which we literally did a few years back here in New Jersey): it could have a high impact on health & safety and a high impact on availability but a low impact on reputation. Your clients would probably understand if you had excessive downtime due to an “act of God” … unless people were hurt or killed because you failed in some major way to put controls in place deal with the hurricane’s impact.
The bottom line here is just to get everybody thinking and talking clearly about your organization’s specific risk probabilities and impacts in a useful way. Starting simple doesn’t mean your results will be simplistic or less meaningful. Just the opposite: starting simple can yield clarity and a solid foundation for risk remediation. Over time you can add complexities and refine outcomes if that proves to be helpful.
To start a conversation about risk assessment issues and variables for your organization, contact Pivot Point Security.
Potential Impact Definitions for Security & Business Objectives
| Security & Business Objectives | Negligible Impact | Low Impact | Medium Impact | High Impact | Critical Impact |
|---|---|---|---|---|---|
| Confidentiality | The unauthorized disclosure of information could be expected to have a negligible adverse effect on organizational operations, organizational assets, or individuals. Example(s): Exposure of information that is already public record |
The unauthorized disclosure of information could be expected to have a minimal adverse effect on organizational operations, organizational assets, or individuals. | The unauthorized disclosure of information could be expected to have a moderate adverse effect on organizational operations, organizational assets, or individuals. | The unauthorized disclosure of information could be expected to have a serious adverse effect on organizational operations, organizational assets, or individuals. | The unauthorized disclosure of information could be expected to have a severe adverse effect on organizational operations, organizational assets, or individuals. Example(s): Damage to client trust |
| Integrity | The unauthorized modification or destruction of information could be expected to have a negligible adverse effect on organizational operations, organizational assets, or individuals. | The unauthorized modification or destruction of information could be expected to have a minimal adverse effect on organizational operations, organizational assets, or individuals. Example(s): Client inconvenienced (e.g. additional copy of ESI required for Litigation Support) |
The unauthorized modification or destruction of information could be expected to have a moderate adverse effect on organizational operations, organizational assets, or individuals. | The unauthorized modification or destruction of information could be expected to have a serious adverse effect on organizational operations, organizational assets, or individuals. | The unauthorized modification or destruction of information could be expected to have a severe adverse effect on organizational operations, organizational assets, or individuals. Examples: Impaired rights of client, Missed deadlines for court filings |
| Availability | The disruption of access to or use of information or an information system could be expected to have a negligible adverse effect on organizational operations, organizational assets, or individuals. | The disruption of access to or use of information or an information system could be expected to have a minimal adverse effect on organizational operations, organizational assets, or individuals. | The disruption of access to or use of information or an information system could be expected to have a moderate adverse effect on organizational operations, organizational assets, or individuals. | The disruption of access to or use of information or an information system could be expected to have a serious adverse effect on organizational operations, organizational assets, or individuals. | The disruption of access to or use of information or an information system could be expected to have a severe adverse effect on organizational operations, organizational assets, or individuals. Examples: Unable to file by deadline, Missed appearances in court |
| Reputation & Customer Confidence | Reputation is negligibly affected; no effort or expense is required to recover. Less than 2% reduction in customers due to loss of confidence |
Reputation is minimally affected; little or no effort or expense is required to recover. Less than 2 to 4% reduction in customers due to loss of confidence |
Reputation is damaged, and some effort and expense is required to recover. 4 to 6% reduction in customers due to loss of confidence |
Reputation is damaged, and significant effort and expense is required to recover. More than 6% reduction in customers due to loss of confidence |
Reputation is irrevocably destroyed or damaged. More than 6% reduction in customers due to loss of confidence |
| Legal | No queries from government or other investigative organizations. No lawsuit(s) are filed against the organization |
No queries from government or other investigative organizations. Frivolous lawsuit(s) are filed against the organization |
No queries from government or other investigative organizations. Frivolous lawsuit(s) are filed against the organization |
Government or other investigative organization initiates a cursory investigation into a specific organizational practices. Non-frivolous lawsuit(s) filed for amounts exceeding insurance coverage,Example(s): Malpractice lawsuit, ethical violations |
Government or other investigative organization initiates a high-profile, in-depth investigation across organizational practices. Non-frivolous lawsuit(s) filed for amounts exceeding insurance coverage, causing significant financial impact to the organization Example(s): Malpractice lawsuit, ethical violations |
| Productivity | Less than 2 hours lost per affected employee | 2 to 3 hours lost per affected employee | 3 to 4 hours lost per affected employee | 3 to 5 hours lost per affected employee | More than 5 hours lost per affected employee |
| Financial | Increase of less than 2% in yearly operating costs | Yearly operating costs increase by 2 to 4%. | Yearly operating costs increase by 4 to 6%. | Yearly operating costs increase by 6 to 8%. | Yearly operating costs increase by more than 8%. |
| Health & Safety | No loss or significant threat to customers’ or staff members’ lives Minimal, immediately treatable degradation in customers’ or staff members’ health with insignificant Safety questioned |
No loss, but potential threat to customers’ or staff members’ lives Moderate, treatable degradation in customers’ or staff members’ health with recovery within four days Safety questioned |
Customers’ or staff members’ lives are threatened, but they will recover after receiving medical treatment. Temporary or recover-able impairment of customers’ or staff members’ health Safety affected |
Customers’ or staff members’ lives are threatened, potential impairment after medical treatment. Potential, long term impairment of customers’ or staff members’ health Safety violated |
Loss of customers’ or staff members’ lives Permanent impairment of significant aspects of customers’ or staff members’ health Safety violated |