Last Updated on April 14, 2025
Recently one of our clients, a local government entity, was the target of a long and intense distributed denial of service (DDOS) attack—a deliberate attempt to make a website unavailable to legitimate users by overwhelming it with bogus traffic from multiple sources. A coordinated botnet hit them with several hundred million connection attempts per second, completely overwhelming their local equipment.
Most SMBs think they won’t get hit with a DDOS attack… until they do. DDOS attacks are a fact of life for organizations of all sizes these days. The impacts run the gamut from loss of revenue to organizational paralysis. LOT Polish Airlines recently stranded over a thousand passengers in Warsaw after a DDOS blitz impeded its ability to produce flight plans for departing aircraft.
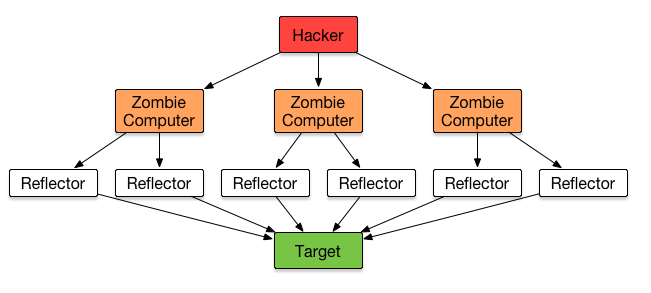
The motives for DDOS attacks range from political (as was the case for our client) to personal to financial to “script kiddie” vandalism. Extortion is increasingly popular. These attacks require so little in the way of technical skill that nearly anyone can launch one. The following illustration shows how DDOS attacks work.
Hackers can simply rent botnets for few hundred dollars to coordinate the attack, or implement a program like Low Orbit Ion Cannon. A single attacker with a home fiber Internet connection could easily tank an unprotected website.
How can SMBs keep their networks operational in the face of these kinds of attacks, which come from thousands of different IP addresses? Even if you set your firewall to ignore or drop the right connections, the volume of traffic pushing against your front door will still deny legitimate service requests. For the average SMB with one Internet connection going into one router into one firewall, your only hope is to get your Internet Service Provider (ISP) involved.
In the case of our client, it wasn’t easy to thwart the attack even from upstream, with help from both the ISP and law enforcement. If I request a webpage for legitimate reasons, I look at it for a few seconds and then click off. This attack would request a page and keep requesting pages. The attackers were also spoofing IP addresses, so when it requested a page the web server would try to reply to a different IP address. The goal was simply to generate maximum traffic in both directions.
Fortunately, ISPs have equipment in place to do statistical analysis on incoming data and determine what is legitimate and what should likely be filtered. SMBs should work with their ISPs to purchase a solution or setup a service. Various third-party vendors also offer DDOS protection and mitigation services, though these can be expensive for SMBs.
Whatever approach an SMB takes to addressing DDOS risk, it’s important to recognize that the risk of an attack—and extended downtime—is increasing. Contact Pivot Point Security to talk over a comprehensive network security strategy that mitigates DDOS risk.