Last Updated on April 14, 2025
While an organization might need to comply with potentially many privacy laws, most of them are similar. In fact, many are based on, or a subset of, the EU’s comprehensive GDPR.
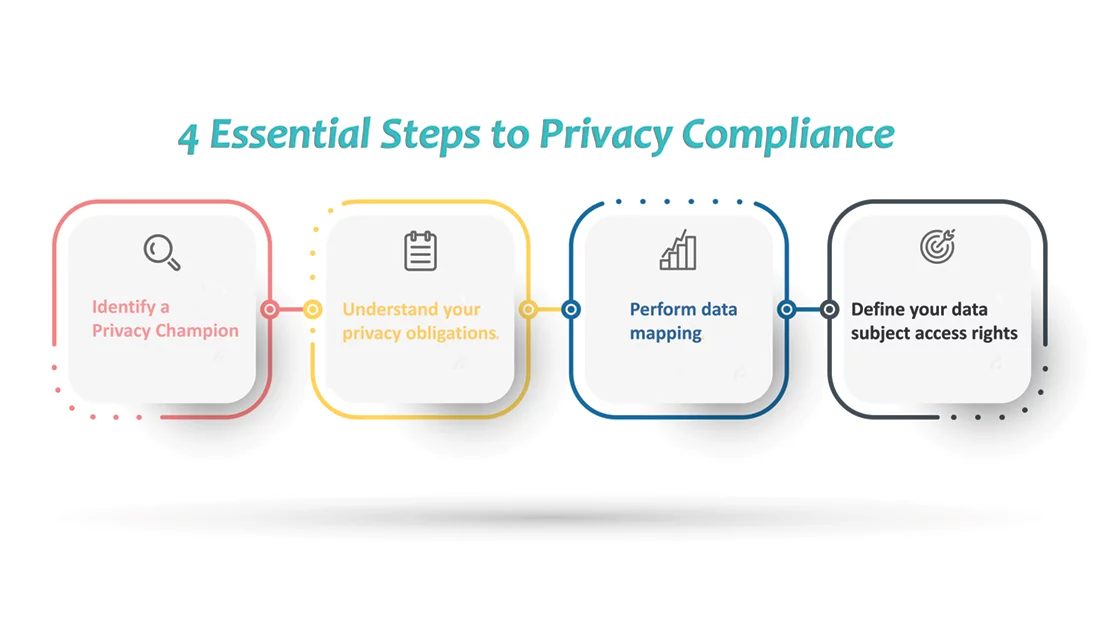
If your company is looking to comply with one or more privacy laws and/or frameworks, where do you start? At a high level, what are the steps you need to wrap your mind (and resources) around?
Jason Powell, GRC and Privacy Consultant at Pivot Point Security, discussed the 4 essential steps every organization must take to achieve privacy compliance with host John Verry, Pivot Point Security CISO and Managing Partner, on a recent episode of The Virtual CISO Podcast.
Step 1: You need a privacy champion
Say your company receives a data processing agreement (DPA) from a major customer. If you can’t say you’re GDPR compliant—or at least “getting there”—you’ll lose that customer.
So, where do you start?
“From the ground up, the thing that most people don’t think about is you’ve got to have a champion in your organization who is preferably a designated, qualified and dedicated privacy stakeholder,” Jason maintains. “That would mostly be in the form of somebody who is a dedicated chief privacy officer (CPO) or just privacy officer.”
“Often, that privacy function, especially in a smaller organization, is tossed over to the chief security officer (CSO) or chief information security officer (CISO), which I think is the wrong way to go,” adds Jason. “But it happens, because sometimes people have to wear multiple hats.”
Step 2: Understand your privacy obligations
Along with finding a privacy champion, you need to understand what applicable laws and contracts require of you around privacy, as well as how your senior management wants to handle privacy.
“It all comes down to requirements, just like any project,” says Jason. “What are you required to do under law? As an example, do you market products or services to people in the European Union? If that’s the case, you are obligated to comply with GDPR as law. If you do business in California, you may have obligations under CCPA, or Virginia or Colorado, any of these states in the US that have new privacy laws. You’ve got to figure out what you are absolutely required to do under law.”
“The next thing is, what are you required to do as part of your contractual obligations?” continues Jason. “If you’re a mid-sized company that makes widgets and you supply them to a large international company, and they state in their contract with you, ‘We have to be GDPR compliant. You’re going to comply with GDPR as well,’ if you want that business, you’re going to have to comply.”
“Then beyond that, what do you, as an organization, feel like you’re obligated to do, whether it’s the CEO or the board of directors or a common understanding by senior management?” Jason indicates. “What’s the right thing for your company to do with regard to security and/or privacy? That’s where you start.”
From there, you need to understand your obligations in complete detail. As Jason states: “Now you have an opportunity to look at a framework or law that you have to comply with. … If you’re required, for instance, to be compliant with GDPR, then get GDPR out. Somebody is going to have to read all 99 articles and preferably all 173 recitals to understand what’s involved. … So, you need to determine the framework or law that you’re operating under.”
“ISO 27701 is a great framework if you want to have a good basic privacy program, but you don’t necessarily have legal and contractual obligations,” clarifies Jason. “You’re doing it because it’s the right thing to do. [With ISO 27701] you have a ready reference to start building that program, using an established framework. That’s a great way to do it.”
Step 3: Perform data mapping
After you know what privacy controls you’re required and/or want to implement, you need to ascertain what data you have and how it’s processed—aka data mapping, akin to or sometimes called a record of processing activities or ROPA.
Where does the personal data you collect come from? Whose data is it? How do you receive it? How do you process it? How do you store it? How do you dispose of it? If you’re a data processor, how do you ensure that you’re meeting your obligations to the data controller?
“Even in a small company, that can be a tedious exercise, because you’re collecting data from the website, from prospective customers, from prospective employees…” Jason concedes. “If you have offered white papers about your product, you might require people to provide their personal information. If you have even a single employee, you are by definition a controller, because you hold data about an employee. It might be yourself if you’re the CEO and sole member of that company, but everybody is a controller.”
“We typically collect lots more personal data than most people realize,” Jason points out. “So, we’ve got to find out where that data comes from, and the purposes of us processing it. And then we have to figure out, are we processing special category data? In other words, is there data that we collect that’s very, very sensitive, that we need to apply an even higher level of control to? This would be things like health data, or data about sexual orientation. Or tracking people through the use of web technology and advertising technologies. You have to determine if you do any of that.”
“If you think you do, then you need to engage in a process called a DPIA or a PIA, depending on the framework,” advises Jason. “It’s a privacy impact assessment. You need to look at what [highly sensitive data] you’re processing, how you’re processing it and how you’re protecting it. And then you need to figure out, can you manage the risks around processing that data? In the EU, if you determine through a PIA that the processing of sensitive data, or special category data as it’s called there, is still a high risk, you have to go to a supervisory authority to get the okay to continue processing that data.”
Step 4: Define your data subject access rights
Along with data mapping, you need to consider data subject access rights. These are the rights that you extend to individuals who contact you about their personal data.
Jason summarizes: “Under GDPR, there’s a long list of data subject access rights. That’s rights like, ‘Hey, John, do you have any personal data that relates to me? If so, I’d like to know what it is and how you’re using it.’ Or, ‘I would like it corrected, because the data that you have about me is not accurate.’ It could be as simple as, you spelled my name wrong. Or, ‘I want it redacted. I don’t think you have any reason to have it anymore. And I want you to remove it from your records.’”
“Then you need to figure out how you’re going to actually get that done,” Jason relates. “That’s an operational issue. Now you have a privacy office with administrators that are doing data subject access requests and responses. Now the program is suddenly much bigger. But those are the initial steps.”
What’s Next?
If you’re helping define or operationalize a privacy strategy for your organization, put this podcast with Jason Powell on your must-listen list: https://www.pivotpointsecurity.com/podcasts/ep66-jason-powell-private-practices-how-to-prioritize-privacy-in-your-organization/
Looking for more strategic guidance on privacy compliance? Try this related post: https://www.pivotpointsecurity.com/how-privacy-is-driving-the-need-for-information-governance/