Last Updated on April 21, 2010

View our free ISO 27001 downloadable resources »
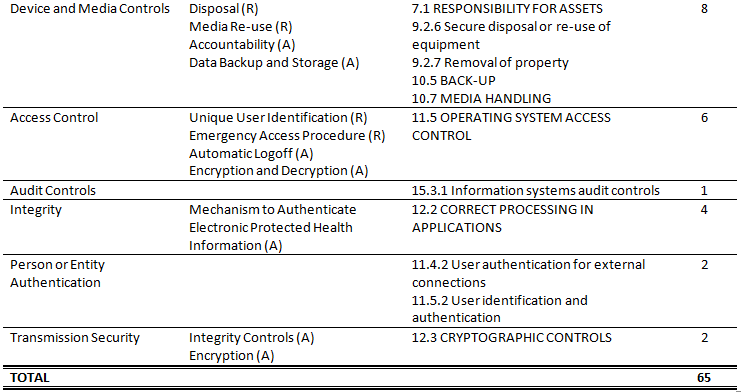
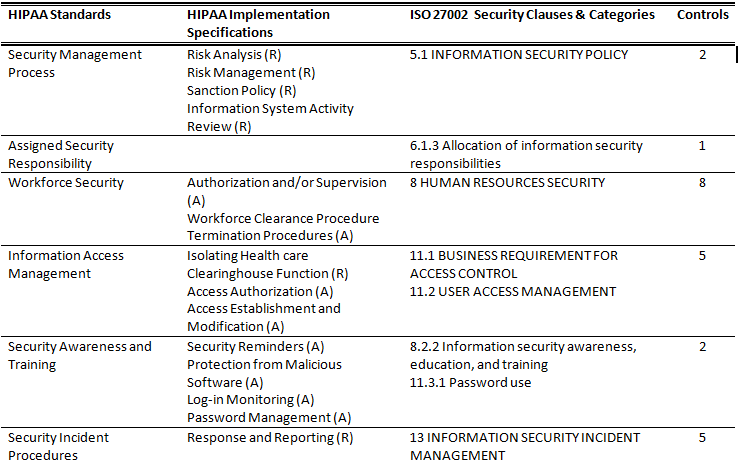
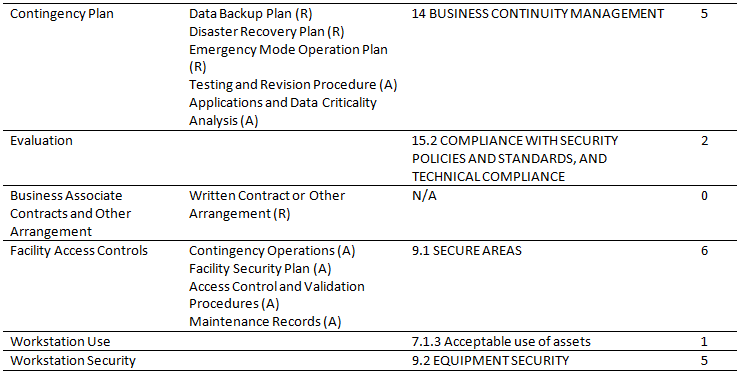
Our Principal Enterprise Security Consultant, John Verry, said he needed to know how the HIPAA Security Rule compared to ISO 27002 in order to put together a proposal for a prospective client. You can see the result of my investigation described in the table below. Based on my estimation, 65 of the 134 controls in 27002 map to the HIPAA Security Rule’s safeguards. The only HIPAA standard that is not addressed by 27002 is section 164.308(b)(1), “Business Associate Contracts and Other Arrangement.”
As you can tell from our website, Pivot Point is a big supporter of ISO 27001 and 27002 and I think this analysis provides a good justification. If an organization has multiple compliance requirements like HIPAA, PCI-DSS, GLBA, etc., then ISO 27001 and 27002 can centralize and simplify those compliance efforts. As the table below shows, an organization only has to implement less than half of the ISO 27001 security controls and it achieves compliance with a significant set of regulations. I think this is why the Shared Assessments Program, which was founded by America’s leading financial institutions and accounting firms to establish a single standard for managing vendor security risks, decided to expand its membership to include healthcare organizations. The Shared Assessments Program is based on ISO 27001 and provides a simple way for vendors to reduce their compliance costs and manage their security risks. If you’re interested in a more detailed analysis of using ISO 27001 to address HIPAA compliance, see the Shared Assessments Program’s detailed mapping.
Table 1 – Mapping HIPAA to ISO 27002 Security Controls

ISO 27001
ISO 27001 is manageable and not out of reach for anyone! It’s a process made up of things you already know – and things you may already be doing.
Get your ISO 27001 Roadmap – Downloaded over 4,000 times